Tor relays are also referred to as "routers" or "nodes." They receive traffic on the Tor network and pass it along. Check out the Tor website for a more detailed explanation of how Tor works.
There are three kinds of relays that you can run in order to help the Tor network: middle relays, exit relays, and bridges.
Tor helps you hide your IP address and prevent browser fingerprinting, making it more difficult for online trackers and even governments to surveil you.
Tor is used by political activists, whistleblowers, journalists, domestic violence survivors, and average people around the world who need to shield their identities as they read and write online.
https://www.eff.org/torchallenge/
- want2c
- 06-12-2014, 02:14 PM
- jframe2
- 06-12-2014, 05:58 PM
I posted the following in another thread and and just cutting and pasting it here.
"Actually we DO NOT need a bunch Eccie users turning their computers into Tor Relay's.
No offense to people that are not a bit tech savy, but the worst possible thing would be for someone to use the same computer for their Hobby/Eccie world and their civie life and open it up as an indiscriminate Tor Relay.
Tor ONLY assists in communication between parties, it does not prevent evil-doers from attacking the computer acting as a Tor relay. You need to be careful in your settings to assure you are not compromising your own PC if you are acting as a relay."
"Actually we DO NOT need a bunch Eccie users turning their computers into Tor Relay's.
No offense to people that are not a bit tech savy, but the worst possible thing would be for someone to use the same computer for their Hobby/Eccie world and their civie life and open it up as an indiscriminate Tor Relay.
Tor ONLY assists in communication between parties, it does not prevent evil-doers from attacking the computer acting as a Tor relay. You need to be careful in your settings to assure you are not compromising your own PC if you are acting as a relay."
- ck1942
- 06-13-2014, 09:26 AM
Well said, jframe2!
What we really need to remembers, both providers and hobbyists, is personal hobby security as well as personal RW security. Giving out or collecting and keeping too much info is what usually gets any of us compromised.
And TORs work best with computers, not so much with cellphones or smart phones or tablets.
Thing is, while a TOR may hide your IP -- TORs don't necessarily conceal the data traffic.
So what you see me typing here, even if via TOR, is still very visible to anyone passing by. And, if there's a sniffer intercepting the traffic between my keyboard and this website, all of the traffic can be very visible to the interloper, and although the IPs may be disguised, those can be resolved or solved eventually.
Keeping your keyboard(s) secure is way more important, imo.
What we really need to remembers, both providers and hobbyists, is personal hobby security as well as personal RW security. Giving out or collecting and keeping too much info is what usually gets any of us compromised.
And TORs work best with computers, not so much with cellphones or smart phones or tablets.
Thing is, while a TOR may hide your IP -- TORs don't necessarily conceal the data traffic.
So what you see me typing here, even if via TOR, is still very visible to anyone passing by. And, if there's a sniffer intercepting the traffic between my keyboard and this website, all of the traffic can be very visible to the interloper, and although the IPs may be disguised, those can be resolved or solved eventually.
Keeping your keyboard(s) secure is way more important, imo.
- BigTitsNut
- 06-24-2014, 01:26 AM
Actually TOR encrypts traffic between each relay point but traffic from your computer to the first TOR network relay may or may not be encrypted and the traffic from the last TOR network computer to the website you wanted to look at. It's true that it's not perfect but it's better than leaving a complete plain text trail online that can point back to you like a big neon arrow..
See https://www.torproject.org/about/overview.html.en
See https://www.torproject.org/about/overview.html.en
- Solitaire
- 06-24-2014, 12:19 PM
so... if I'm reading you right... for sake of example - if I am at a public library, and I use TOR: 1. will it allow me to access sites that would otherwise be blocked? and 2. would the administrator be able to see what sites I am accessing while on their network, and 3. If not TOR, then what program would facilitate this?
- GneissGuy
- 07-05-2014, 02:28 PM
So what you see me typing here, even if via TOR, is still very visible to anyone passing by. And, if there's a sniffer intercepting the traffic between my keyboard and this website, all of the traffic can be very visible to the interloper, and although the IPs may be disguised, those can be resolved or solved eventually. Originally Posted by ck1942If your computer is set up right, and you use it right, TOR basically prevents anyone from snooping on your web browsing unless they have access to the segment of the network between the TOR exit node and the website you're going to.
For instance, your ISP can't see your data, your passwords, or even which web site you're going to. They can tell you're using TOR.
The above applies to people snooping on your WiFi, "rogue" WiFi hotspots, etc.
It doesn't cover every risk. It's not necessarily unbreakable. It's not perfect, but what is. It's valuable.
Note that the above comments are about the protection given by using TOR, not about whether you should run a TOR node yourself as part of "the TOR Challenge."
- GneissGuy
- 07-05-2014, 02:32 PM
so... if I'm reading you right... for sake of example - if I am at a public library, and I use TOR: 1. will it allow me to access sites that would otherwise be blocked? and 2. would the administrator be able to see what sites I am accessing while on their network, and 3. If not TOR, then what program would facilitate this? Originally Posted by SolitaireIf you're logged into their computer, they can log and see everything you do, including logging your passwords. They probably won't allow you to run TOR on their computer. It's even possible that one of the other computer users has put spyware on the library computer and is logging all this stuff.
If you're using their WiFi or network with your own computer, they can probably block your access to TOR and other proxy services. They probably have such services on their blocked IP address list.
- GneissGuy
- 07-05-2014, 03:21 PM
Adding TOR gives you a lot of added protection to some threats, but it's not perfect.
Assume you log in to a web site through a valid TOR network with a valid TOR client.
Also assume your computer isn't compromised. (i.e. no spyware on your computer.)
Data goes through multiple computers, referred to as relays or nodes.
Your traffic (data) is encrypted by your computer and goes to an input relay. That relay node re-encrypts the data and passes the data to another "intermediate" relay. I think TOR sends the data through at least two intermediate relays. The last intermediate relay encrypts the data and sends it to an "exit" relay or TOR exit node.
The last exit node sends the data unencrypted to the web site.
When the exit node responds and sends data back, it sends unencrypted data back to the exit node, and it encrypts it and forwards it back through the same chain.
If you log into www.bob.com through TOR, the data between the exit node and www.bob.com is visible and readable to anyone just as if you connected to www.bob.com directly.
Anyone snooping at www.bob.com, the TOR exit node, or anywhere between those two nodes can see all your traffic. However, they cannot see your originating IP address.
Anyone snooping on your network, on any of the TOR relays other than the exit node, or any of the network cannot see your data or that coming back from the web site. They cannot see which web site you are connecting to.
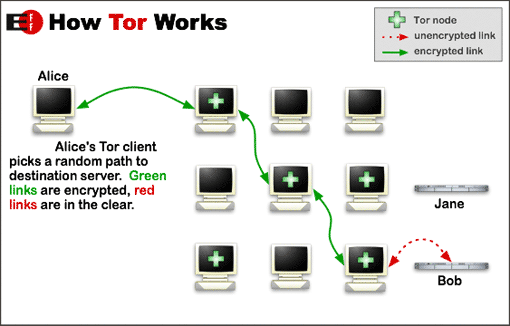
Note that the link between the last node and the web site is in the clear and can be read by anyone who can see that data. The way to fix this is for the web site to support https. This encrypts all traffic on top of what TOR does. https prevents snooping on the last link in the chain and keeps anyone from snooping unless they have access to the internals of the computers at www.bob.com.
There are some potential weaknesses in the above system.
There could be some sort of hidden malicious code built into the TOR system.
There could be some sort of flaw, either malicious or accidental, in the code.
There could be a weakness, either malicious or accidental, in the math for the encryption used.
There are some more esoteric ways to attack a TOR connection, but they usually require quite a bit of resources on the part of the attacker.
Probably the biggest risk is a rogue TOR exit node. If the TOR exit node is compromised, it can see all your web browsing just like a wiretap at the web site's ISP can. That's why https is so important.
Assume you log in to a web site through a valid TOR network with a valid TOR client.
Also assume your computer isn't compromised. (i.e. no spyware on your computer.)
Data goes through multiple computers, referred to as relays or nodes.
Your traffic (data) is encrypted by your computer and goes to an input relay. That relay node re-encrypts the data and passes the data to another "intermediate" relay. I think TOR sends the data through at least two intermediate relays. The last intermediate relay encrypts the data and sends it to an "exit" relay or TOR exit node.
The last exit node sends the data unencrypted to the web site.
When the exit node responds and sends data back, it sends unencrypted data back to the exit node, and it encrypts it and forwards it back through the same chain.
If you log into www.bob.com through TOR, the data between the exit node and www.bob.com is visible and readable to anyone just as if you connected to www.bob.com directly.
Anyone snooping at www.bob.com, the TOR exit node, or anywhere between those two nodes can see all your traffic. However, they cannot see your originating IP address.
Anyone snooping on your network, on any of the TOR relays other than the exit node, or any of the network cannot see your data or that coming back from the web site. They cannot see which web site you are connecting to.

Note that the link between the last node and the web site is in the clear and can be read by anyone who can see that data. The way to fix this is for the web site to support https. This encrypts all traffic on top of what TOR does. https prevents snooping on the last link in the chain and keeps anyone from snooping unless they have access to the internals of the computers at www.bob.com.
There are some potential weaknesses in the above system.
There could be some sort of hidden malicious code built into the TOR system.
There could be some sort of flaw, either malicious or accidental, in the code.
There could be a weakness, either malicious or accidental, in the math for the encryption used.
There are some more esoteric ways to attack a TOR connection, but they usually require quite a bit of resources on the part of the attacker.
Probably the biggest risk is a rogue TOR exit node. If the TOR exit node is compromised, it can see all your web browsing just like a wiretap at the web site's ISP can. That's why https is so important.
- jframe2
- 07-07-2014, 04:59 AM
GeneissGuy has put together a very good and descriptive bit on what/how TOR works.
We can now only hope that people will read all the messages and think about what it means before they start the "what if" questions.
Hats off to you GG.
We can now only hope that people will read all the messages and think about what it means before they start the "what if" questions.
Hats off to you GG.
- Gollum
- 07-12-2014, 02:24 PM
TAILS works pretty good for TOR online anonymity on the go (e.g., a laptop). It takes some amount of tech savvy, however, to use it properly.
https://tails.boum.org/
https://tails.boum.org/
- Doglegg
- 07-13-2014, 09:13 AM
Thanks to GneissGuy and Gollum, the information is accurate.
In order to use a 'LiveCD' operating system on a public computer, e.g. Library/Hotel, access to the BIOS is necessary to change the boot parameters from the computer hard drive to the CD-ROM or USB. This requires the computer to not have a locked BIOS. Some do, most do not.
After using a 'LiveCD' OS a few times it would get easier.
Having searched through a few hotel computers, it is fairly easy to pick out the working girls, the sites used and their advertisement pictures. Good stuff for the curious.
The key to proxy blockers is having a secured virtual private network to a VPN router/server. It appears the product Gollum linked does this to a TOR network.
It is very possible that this will work until the proxy or firewall updates block the IP of the VPN, in which case an update of the product will have to provide a new address to bypass the blockade.
Thanks for sharing the info.
Dogg
In order to use a 'LiveCD' operating system on a public computer, e.g. Library/Hotel, access to the BIOS is necessary to change the boot parameters from the computer hard drive to the CD-ROM or USB. This requires the computer to not have a locked BIOS. Some do, most do not.
After using a 'LiveCD' OS a few times it would get easier.
Having searched through a few hotel computers, it is fairly easy to pick out the working girls, the sites used and their advertisement pictures. Good stuff for the curious.
The key to proxy blockers is having a secured virtual private network to a VPN router/server. It appears the product Gollum linked does this to a TOR network.
It is very possible that this will work until the proxy or firewall updates block the IP of the VPN, in which case an update of the product will have to provide a new address to bypass the blockade.
Thanks for sharing the info.
Dogg
- DangedDragon
- 07-13-2014, 10:26 PM
so... if I'm reading you right... for sake of example - if I am at a public library, and I use TOR: 1. will it allow me to access sites that would otherwise be blocked? and 2. would the administrator be able to see what sites I am accessing while on their network, and 3. If not TOR, then what program would facilitate this? Originally Posted by SolitaireHaving set up systems for libraries and schools several times...here's what "should" happen.
1. Tor may be blocked. Some libraries actually install Tor for private browsing, which is a topic frequently discussed in their IT forums.
2. Yes - They log websites visited, review reports, and adjust firewall/proxy/filter setting appropriately. (Note: Many libraries DO NOT censor adult access, but may filter out images from certain adult sites.)
3. NONE
In general librarians are very anti-censorship, preferring to give complete access to adults, but with a protective eye towards other patrons.
Libraries and schools "can be" very strict on their rules, logging, and filtering. Schools more than libraries. Libraries are virtually required to log and filter if they accept federal funds, which most do. Schools are in the same boat. If they accept federal funds they are filtering and logging. (Note: the filters may be very lenient..) I cannot comment on University settings, since I never setup any of their systems.
They can pull reports on which computer accessed what sites at what time and cross reference it to the person who "checked-in" to that computer. I have never seen LE request them to do it, but I know it can be done because I taught a couple librarians how to pull the reports, and yes, they do review those reports frequently.
Hotels could install similar systems, but I never had any request it. They usually wanted to focus on only two factors. Protect our office systems and make it cheap. Same with fast food and restaurants where I installed systems..cheap without logging was the rule.
If you are wondering about bypassing those filters, just be aware that will still get logged. It may show up as VPN traffic, or another type of traffic, but that will key a good admin to keep a closer eye on that user, which often leads to screen recording.
Libraries are a horrible place to do anything questionable.